In today’s cloud-native landscape, maintaining robust monitoring capabilities is crucial for ensuring the reliability and performance of your Azure resources. Azure Monitor Baseline Alerts offer a standardized set of alerts based on best practices, facilitating proactive monitoring and early issue detection.
Part of the Azure landing zone (ALZ) product, Azure Monitor Baseline Alerts aim to simplify the adoption of Azure Monitor. It provides recommended alert rules, packaged into Azure Policy definitions and organized into logical initiatives. This solution offers flexibility, allowing for customization and deployment through various methods.
Currently, Azure Monitor Baseline Alerts are integrated only with the ALZ Portal Accelerator, with plans for integration into Bicep and Terraform ALZ accelerators in the future.
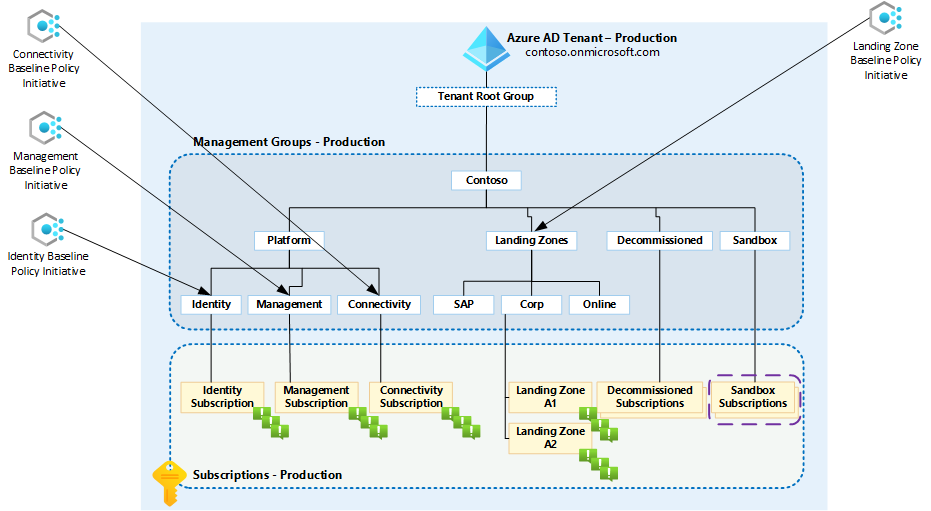
In this blog post, we’ll walk through the process of deploying Azure Monitor Baseline Alerts using Enterprise Policy as Code (EPAC). Leveraging EPAC streamlines policy deployment, ensures consistency across environments, and facilitates automation. We will focus solely on deploying and configuring AMBA without using the Portal Accelerator to avoid any potential disruption to our existing landscape.
Disclaimer
The following solution is provided as-is, with no guarantees. It is strongly recommended to test it first in a non-production environment before implementing it in your production environment.
Please note that this solution will incur costs, which will be added on top of your monthly Azure spending.
Prerequisites
Before we dive into the deployment process, ensure you have the following prerequisites in place:
- Access to at least one Azure subscription.
- Installation of the Git CLI.
- Installation of the Az PowerShell module.
- Installation of the EnterprisePolicyAsCode PowerShell module (refer also to step 1 down below).
- A Git clone of the Enterprise Azure Policy as Code repository (refer also to step 1 down below).
- Preferably a Code Editor like Visual Studio Code.
Step 1: Setting up EPAC
The first step is to set up EPAC definitions to define the policies and configurations you want to enforce. Clone the Enterprise Azure Policy as Code repository from GitHub:
git clone https://github.com/Azure/enterprise-azure-policy-as-code.gitNext, install and import the EnterprisePolicyAsCode PowerShell module from an elevated PowerShell prompt or using a Terminal window from Visual Studio Code:
### Install EPAC PowerShell Module ###
Install-Module EnterprisePolicyAsCode -Verbose
### Import EPAC PowerShell Module ###
Import-Module EnterprisePolicyAsCodeNavigate to the EPAC folder and create a definitions folder.
### Build EPAC definitions folder ###
Build-DeploymentPlans -DefinitionsRootFolder Definitions -OutputFolder OutputNow, configure the global settings in the global-settings.json file under the definitions folder. This file specifies the target Azure environment, tenant ID, deployment scope, managed identities location, and desired deployment state. Here’s a sample down below:
{
"$schema": "https://raw.githubusercontent.com/Azure/enterprise-azure-policy-as-code/main/Schemas/global-settings-schema.json",
"pacOwnerId" : "platform-team",
"pacEnvironments": [
{
"pacSelector": "myazureenvironment",
"cloud": "AzureCloud",
"tenantId": "your-tenant-id",
"deploymentRootScope": "/providers/Microsoft.Management/managementGroups/101",
"desiredState": {
"strategy": "ownedOnly"
}
}
],
"managedIdentityLocations" : {
"*": "westeurope"
}
}
Before proceeding, please replace the placeholders in the snippet above: on line 4 (platform-team), line 7 (myazureenvironment), line 9 (your-tenant-id), and line 10 (replace it with deployment scope id). For line 11 (strategy), refer to this article for getting a better understanding of the desired state strategy.
Step 2: Deploying AMBA policy definitions and assignments with EPAC
Next, download and copy the contents of the definitions folder from amba-export/Definitions at main · anwather/amba-export · GitHub to the definitions folder we created earlier. These are the AMBA definitions, made especially for use by EPAC.
Now navigate to the folder policyAssignments under Definitions, you should see the following 5 files:
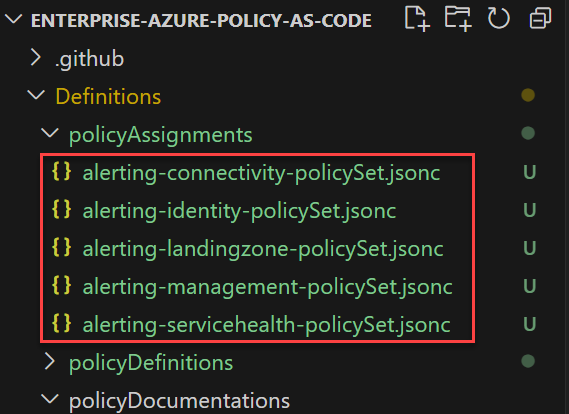
In each of the above files, adjust the scope, managedIdentityLocations, and parameters to fit your needs.
Note n1: If you are using Enterprise Scale, then adjust the assignments for each file accordingly, e.g for configuration alerting-management-policySet.jsonc change the scope to management management group.
Note n2: If you are using ALZ for small enterprises, adjust connectivity, identity and management to be deployed to Platform management group.
Note n3: If you are using a custom archetype, then just the deployment scope to according to your preference and your environment.
Here is a sample of alerting-servicehealth-policySet.jsonc:
{
"$schema": "https://raw.githubusercontent.com/Azure/enterprise-azure-policy-as-code/main/Schemas/policy-assignment-schema.json",
"nodeName": "/root",
"definitionEntry": {
"policySetName": "Alerting-ServiceHealth",
"displayName": "Deploy Azure Monitor Baseline Alerts for Service Health",
"nonComplianceMessages": [
{
"policyDefinitionReferenceId": null,
"message": "Alerting must be deployed to Azure services."
}
]
},
"assignment": {
"name": "Deploy-AMBA-SvcHealth",
"displayName": "Deploy Azure Monitor Baseline Alerts for Service Health",
"description": "Initiative to deploy AMBA Service Health alerts to Azure services"
},
"metadata": {
"_deployed_by_amba": true
},
"parameters": {
"svcHlthAdvisoryAlertState": "true",
"alzMonitorResourceGroupName": "rg-amba-monitor-weu-01",
"svcHlthIncidentAlertState": "true",
"svcHlthMaintenanceAlertState": "true",
"svcHlthSecAdvisoryAlertState": "true",
"alzMonitorResourceGroupLocation": "eastus",
"resHlthUnhealthyAlertState": "true",
"alzMonitorResourceGroupTags": {
"Project": "alz-monitor"
},
"alzMonitorActionGroupEmail": "[email protected]"
},
"scope": {
"myazureenvironment": [
"/providers/Microsoft.Management/managementGroups/101"
]
}
}Once the AMBA definitions are configured, it’s time to deploy them to your Azure environment. Use the following commands to deploy policy and role assignment plans:
### Login to the Azure environment ###
Login-AzAccount -TenantId <your tenant id goes here> -DeviceCode
### List the Azure Subscriptions that you currently have access to, make a note of the subscription that you would like the AMBA resources to be created to ###
Get-AzContext
### Switch to the Azure Subscription ###
Set-AzContext -SubscriptionId <subscription id goes here>
### Deploy Policy,Policy Set Definitions and assignments using EPAC ###
Deploy-PolicyPlan -pacEnvironmentSelector <pacenvironment name goes here> -DefinitionsRootFolder .\Definitions -InputFolder .\Output
### Deploy Policy Remediation Role Assignments using EPAC ###
Deploy-RolesPlan -pacEnvironmentSelector <pacenvironment name goes here> -DefinitionsRootFolder .\Definitions -InputFolder .\OutputStep 3: Creating Azure Remediation Tasks
After deploying the AMBA definitions and assignments, you can proceed with creating Azure Remediation Tasks to enforce the policies and establish the required resources and configurations as defined in EPAC configuration. Specify the environment selector and the root folder containing the definitions accordingly:
### Deploy Policy Remediation Tasks using EPAC ###
Create-AzRemediationTasks -pacEnvironmentSelector <pacenvironment name goes here> -DefinitionsRootFolder .\DefinitionsNow let’s take a look at what has been deployed. Navigate to Azure Monitor, click on the Alerts blade, and then proceed to Alert rules and processing rules.
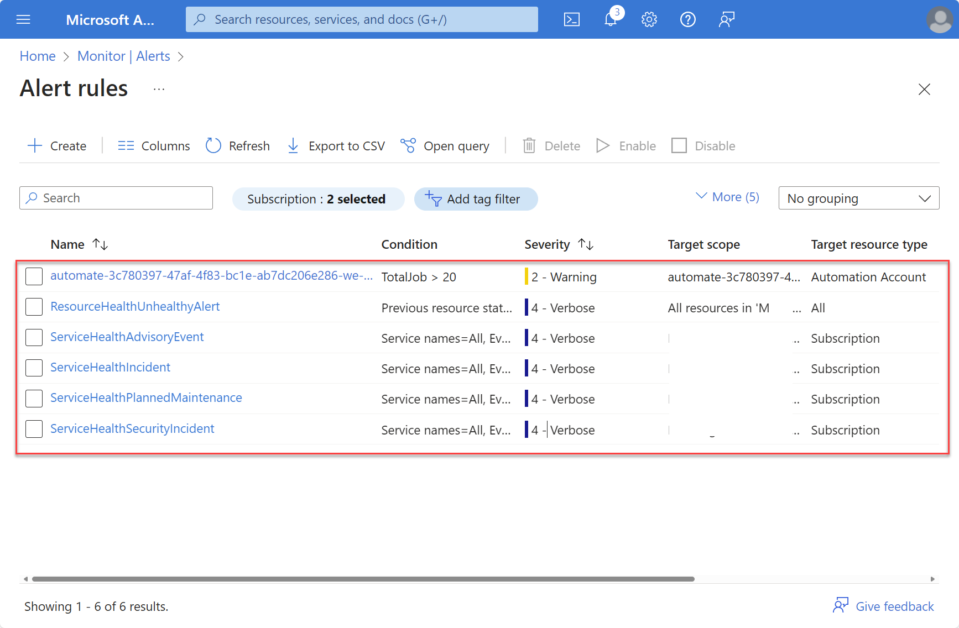
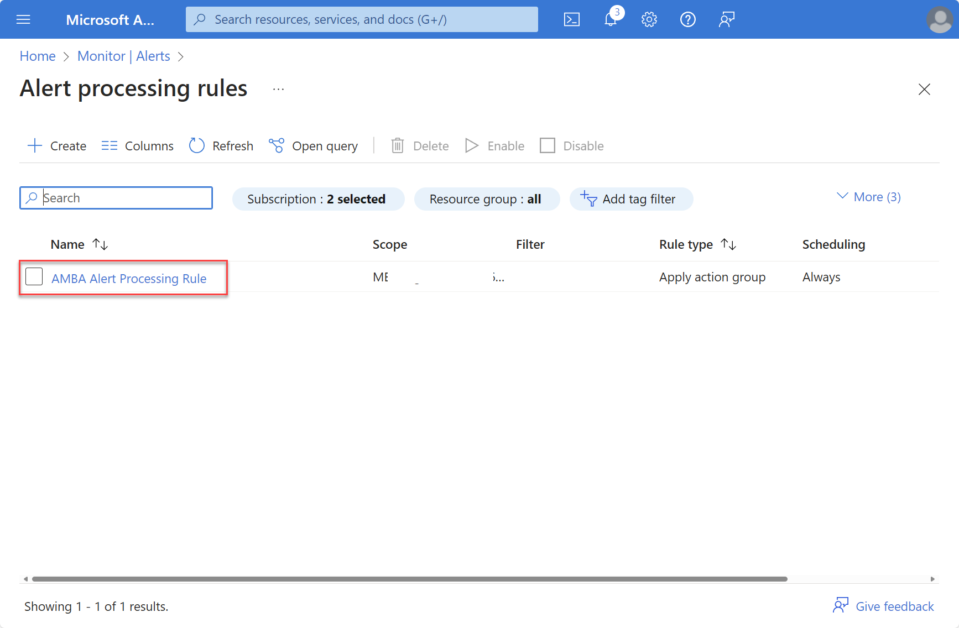
In the subscription we selected earlier as the context for deploying the required AMBA resources, you will find a newly created resource group with the name specified in the configuration.
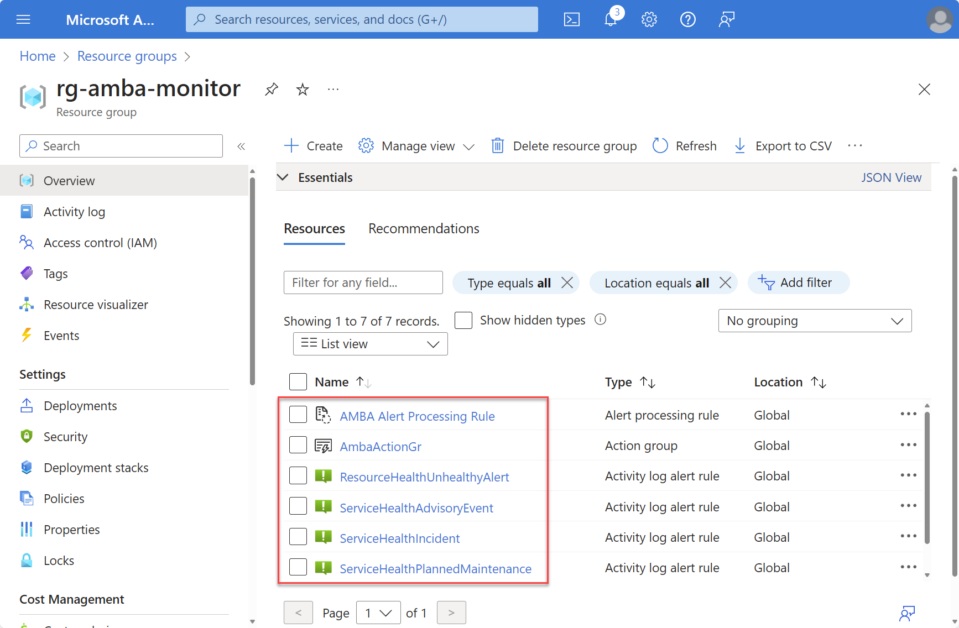
Conclusion
By leveraging Enterprise Policy as Code (EPAC), you can automate the deployment and enforcement of Azure Monitor Baseline Alerts, ensuring consistent monitoring across your Azure environment. This approach not only streamlines policy management but also enhances the reliability and resilience of your cloud infrastructure
Incorporating EPAC into your Azure governance strategy will contribute to maintaining compliance, improving security, and optimizing resource utilization effectively. With EPAC, managing Azure policies becomes more agile, scalable, and manageable, empowering organizations to achieve their cloud objectives with confidence.
Additional Resources on AMBA and EPAC
- Azure Monitor Baseline Alerts
- Enterprise Policy As Code
- Azure Monitor Baseline Alerts Policy Export in EPAC format


You must be logged in to post a comment.