Guarded fabric can run three types of virtual machines:
• Unprotected virtual machines: These virtual machines are standard Generation 1 or Generation 2 virtual machines that do not have any additional level of protection. Such virtual machines can run on any Hyper-V host and not only on guarded fabric.
• Encryption-supported virtual machines: These are Generation 2 virtual machines that have vTPM that a virtual machine can use to encrypt the content of its virtual hard disk. You also can encrypt state and migration traffic for encryption-supported virtual machines. A virtualization administrator can access these virtual machines in the same way as accessing unprotected virtual machines and can run them on Hyper-V hosts that are not part of a guarded fabric. A Hyper-V host can present virtual TPM to encryption-supported virtual machines without requiring physical TPM on the Hyper-V host.
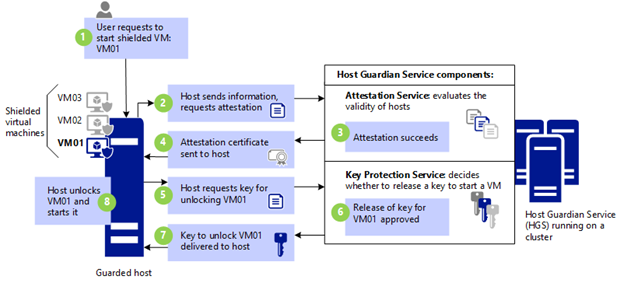
• Shielded virtual machines: Shielded virtual machines include all the protection of encryption supported virtual machines and additional protection. Shielded virtual machines can start only if you run it on the Hyper-V host that is part of guarded fabric and it meets attestation requirements. You can access shielded virtual machines only over a network, for example by using Remote Desktop Connection you cannot access them by using Virtual Machine Connection or PowerShell Direct.
More posts on Windows Server 2016 Virtualization:
- Installing the Hyper-V role on Windows Server 2016
- Production Checkpoints on Hyper-V 2016
- Host Resource Protection on Hyper-V 2016
- Node fairness on Hyper-V 2016, VM Load Balancing for the SMB!
- AVMA on Windows Server 2016
- Run Hyper-V in a Virtual Machine with Nested Virtualization
- Manage Windows Virtual Machines with PowerShell Direct